Internet Management

Navigating the Digital Ocean: A Comprehensive Guide to Internet Management
In today’s hyper-connected world, the internet is no longer a luxury but a fundamental utility, akin to electricity or water. Whether for individuals, businesses, or organizations, effective internet management is crucial for ensuring reliable access, optimizing performance, maintaining security, and controlling costs. It encompasses a wide range of practices and technologies aimed at governing how we connect to, utilize, and interact with the vast digital landscape.
Understanding the Scope of Internet Management
Internet management is a multifaceted discipline that involves overseeing various aspects of internet connectivity and usage. It’s not just about having an internet connection; it’s about strategically planning, implementing, and maintaining the infrastructure and policies that govern how the internet is accessed and used. This includes:
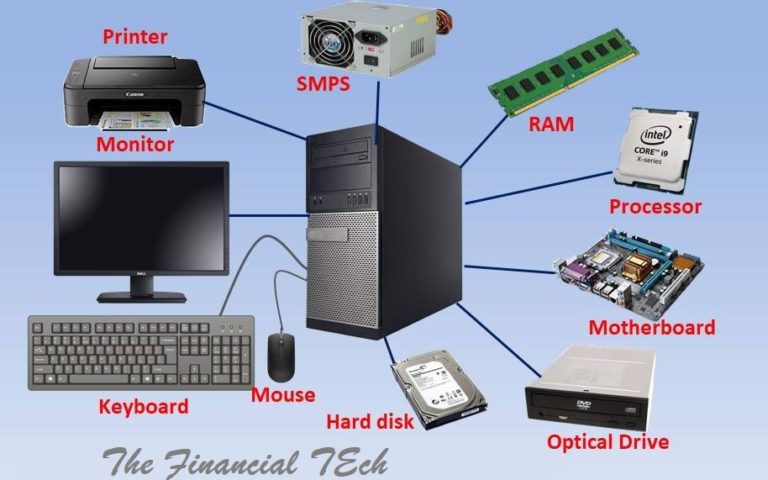
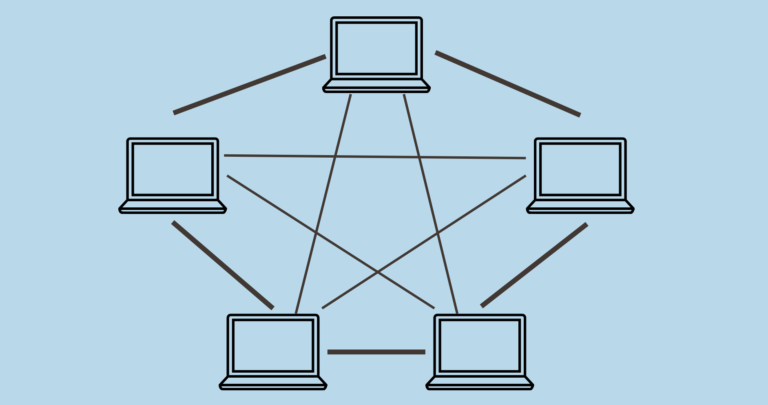
- Network Infrastructure Management: Managing the physical and logical components that enable internet access, such as routers, switches, modems, cables, and wireless access points.
- Bandwidth Management: Monitoring and controlling the amount of data transmitted over an internet connection to ensure optimal performance and prevent congestion.
- Security Management: Implementing measures to protect against cyber threats, malware, unauthorized access, and data breaches.
- Access Control: Defining and enforcing policies regarding who can access the internet and what resources they can access.
- Usage Monitoring and Reporting: Tracking internet usage patterns for capacity planning, cost control, and identifying potential issues.
- Content Filtering and Management: Controlling the types of content that can be accessed over the network, often for security, productivity, or compliance reasons.
- Troubleshooting and Support: Addressing connectivity issues and providing technical assistance to users.
- Cost Management: Optimizing internet service plans and usage to minimize expenses.
- Policy Development and Enforcement: Establishing guidelines for acceptable internet use and ensuring compliance.
Key Areas of Internet Management
To effectively manage internet resources, attention must be paid to several key areas:
Network Infrastructure:
- Hardware Selection and Configuration: Choosing the right routers, switches, firewalls, and other network devices based on the number of users, bandwidth requirements, and security needs. Proper configuration is essential for optimal performance and security.
- Wireless Network Management: Setting up and managing Wi-Fi networks, including access point placement, channel selection, security protocols (e.g., WPA3), and guest network management.
- Cabling and Physical Infrastructure: Ensuring proper installation and maintenance of physical cables and connections to prevent disruptions.
- Hardware Selection and Configuration: Choosing the right routers, switches, firewalls, and other network devices based on the number of users, bandwidth requirements, and security needs. Proper configuration is essential for optimal performance and security.
Bandwidth Management:
- Traffic Shaping and Prioritization: Implementing techniques to prioritize critical network traffic (e.g., VoIP, video conferencing) over less time-sensitive data to ensure a smooth user experience.
- Quality of Service (QoS): Configuring network devices to guarantee a certain level of performance for specific applications or users.
- Bandwidth Monitoring and Throttling: Tracking bandwidth usage to identify heavy users or applications and potentially limiting their bandwidth consumption to prevent network saturation.
- Traffic Shaping and Prioritization: Implementing techniques to prioritize critical network traffic (e.g., VoIP, video conferencing) over less time-sensitive data to ensure a smooth user experience.
Security Management:
- Firewall Configuration: Implementing and maintaining firewalls to control network traffic and block unauthorized access.
- Intrusion Detection and Prevention Systems (IDPS): Deploying systems to monitor network activity for malicious patterns and automatically block or alert administrators to potential threats.
- Malware Protection: Implementing antivirus and anti-malware solutions on end-user devices and network gateways.
- Virtual Private Networks (VPNs): Utilizing VPNs to create secure and encrypted connections for remote access or enhanced privacy.
- Security Audits and Vulnerability Assessments: Regularly assessing the network infrastructure and systems for security weaknesses and addressing them proactively.
- Firewall Configuration: Implementing and maintaining firewalls to control network traffic and block unauthorized access.
Access Control:
- User Authentication and Authorization: Implementing secure methods for verifying user identities (e.g., passwords, multi-factor authentication) and controlling their access to network resources.
- Network Segmentation: Dividing the network into isolated segments to limit the impact of security breaches.
- Guest Network Management: Providing secure and controlled internet access for visitors without compromising the primary network.
Usage Monitoring and Reporting:
- Log Analysis: Collecting and analyzing network traffic logs to identify usage patterns, potential security incidents, and performance bottlenecks.
- Reporting Tools: Utilizing software to generate reports on internet usage, bandwidth consumption, and website access.
- Capacity Planning: Using usage data to forecast future bandwidth needs and plan for network upgrades.
- Log Analysis: Collecting and analyzing network traffic logs to identify usage patterns, potential security incidents, and performance bottlenecks.
Content Filtering and Management:
- Website Blocking: Implementing filters to prevent access to specific websites or categories of content based on security risks, productivity concerns, or compliance requirements.
- Application Control: Managing the types of applications that can be used on the network.
- DNS Filtering: Using DNS-based services to block access to known malicious or inappropriate websites.
- Website Blocking: Implementing filters to prevent access to specific websites or categories of content based on security risks, productivity concerns, or compliance requirements.
Troubleshooting and Support:
- Diagnostic Tools: Utilizing network diagnostic tools to identify and resolve connectivity issues.
- Help Desk Support: Providing technical assistance to users experiencing internet-related problems.
- Remote Access and Management: Using remote management tools to diagnose and resolve issues without physical access to the device.
- Diagnostic Tools: Utilizing network diagnostic tools to identify and resolve connectivity issues.
Cost Management:
- Service Provider Negotiation: Choosing the most cost-effective internet service plans based on bandwidth needs and service level agreements (SLAs).
- Usage Optimization: Implementing policies and technologies to minimize unnecessary bandwidth consumption.
- Cloud Service Cost Management: Monitoring and optimizing the costs associated with cloud-based services that rely on internet connectivity.
Policy Development and Enforcement:
- Acceptable Use Policies (AUPs): Creating clear guidelines for how the internet should be used within an organization or by individuals.
- Enforcement Mechanisms: Implementing technical controls and disciplinary measures to ensure compliance with internet usage policies.
- Regular Policy Review and Updates: Adapting internet usage policies to reflect evolving technologies and security threats.
- Acceptable Use Policies (AUPs): Creating clear guidelines for how the internet should be used within an organization or by individuals.
Why is Effective Internet Management Important?
Effective internet management offers numerous benefits for individuals, businesses, and organizations:
- Enhanced Productivity: Reliable and optimized internet access ensures that users can perform their tasks efficiently without being hampered by slow speeds or connectivity issues.
- Improved Security: Robust security measures protect against cyber threats, data breaches, and malware infections, safeguarding sensitive information and maintaining operational integrity.
- Cost Control: By monitoring usage and optimizing service plans, organizations and individuals can avoid unnecessary expenses and make the most of their internet investments.
- Regulatory Compliance: In many industries, there are regulations regarding data security and internet usage that require effective management practices.
- Optimal Performance: Proper bandwidth management and network infrastructure ensure that applications and services run smoothly and reliably.
- Reduced Downtime: Proactive monitoring and maintenance can help prevent network outages and minimize disruptions.
- Enhanced User Experience: A well-managed internet environment provides a positive and seamless online experience for users.
- Capacity Planning: Understanding usage patterns allows for informed decisions about future bandwidth needs and infrastructure upgrades.
Challenges in Internet Management
Despite its importance, internet management can present several challenges:
- Increasing Bandwidth Demands: The growing use of streaming video, cloud services, and data-intensive applications constantly puts pressure on internet infrastructure.
- Evolving Security Threats: Cyber threats are becoming increasingly sophisticated, requiring continuous vigilance and adaptation of security measures.
- Managing Diverse Devices: The proliferation of smartphones, tablets, laptops, and IoT devices on networks complicates management and security efforts.
- Remote Work and BYOD (Bring Your Own Device): Supporting remote workers and personal devices on the network introduces new security and management complexities.
- Cost Optimization: Balancing the need for high-speed internet with budget constraints can be challenging.
- Keeping Up with Technology: The rapid pace of technological advancements requires continuous learning and adaptation of management strategies.
Best Practices for Internet Management
To overcome these challenges and achieve effective internet management, consider implementing the following best practices:
- Develop a Comprehensive Internet Usage Policy: Clearly define acceptable and unacceptable internet use.
- Implement Strong Security Measures: Employ firewalls, intrusion detection/prevention systems, and malware protection.
- Regularly Monitor Network Performance and Usage: Utilize monitoring tools to track bandwidth, identify bottlenecks, and detect anomalies.
- Implement Bandwidth Management Techniques: Prioritize critical traffic and consider throttling non-essential usage.
- Control Access to Network Resources: Use strong authentication and authorization methods.
- Educate Users on Security Awareness: Train users to recognize and avoid phishing scams and other cyber threats.
- Keep Network Infrastructure Up-to-Date: Regularly patch and update network devices to address security vulnerabilities and improve performance.
- Plan for Future Bandwidth Needs: Anticipate growth in internet usage and plan for necessary upgrades.
- Regularly Review and Update Internet Management Strategies: Adapt to evolving technologies and threats.
- Consider Outsourcing: For organizations lacking the necessary expertise, consider partnering with managed service providers (MSPs) for internet management.
Conclusion
In an increasingly digital world, effective internet management is no longer optional but a necessity for individuals and organizations alike. By understanding the various aspects of internet management, implementing robust strategies, and staying abreast of evolving technologies and threats, we can navigate the digital ocean safely, efficiently, and productively. Whether it’s ensuring a smooth streaming experience at home or maintaining a secure and high-performing network for a business, proactive and comprehensive internet management is the key to harnessing the full power of the internet while mitigating its inherent risks.
OTHER POSTS